防火墙多出口之配置ISP选路实现按运营商转发
了解ISP选路
介绍ISP选路的概述和原理。
概述
ISP选路功能也称为运营商地址库选路功能,当FW作为出口网关设备连接多个ISP网络时,通过ISP选路功能可以使访问特定ISP网络的流量从相应出接口转发,保证流量转发使用最短路径,提高转发效率。
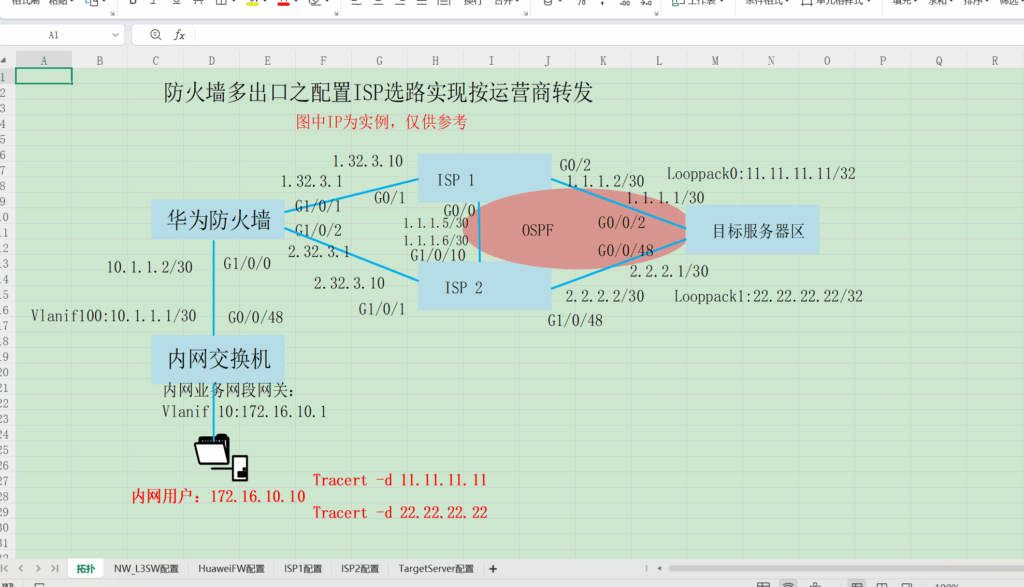
如图1所示,FW拥有两条属于不同ISP网络的出口链路。当内网用户访问ISP2中的Server2时,如果FW上存在等价路由,则FW可以通过两条不同的路径到达Server2,如图1中的路径1和路径2。其中,路径2显然不是最优路径,路径1才是用户所期望的路径。
配置ISP选路功能后,当内网用户访问Server1或Server2时,FW会根据目的地址所在ISP网络选择相应的出接口,从而使访问流量通过最短路径到达服务器,如图1中的路径3和路径1。
ISP选路的原理
ISP选路是基于ISP路由的选路方式,通过批量生成到运营商网络的ISP路由实现访问特定ISP网络的报文都从相应的出接口转发。ISP选路可以单独使用,也可以结合其他智能选路功能一起使用,具体的使用场景分类如表1所示:
| 分类 | 使用场景 |
|---|---|
| ISP选路场景 | 如果用户希望访问特定ISP网络的流量从相应出接口转发,不会绕道其他ISP,可以配置ISP选路功能。 |
| ISP选路+策略路由组合场景 | 如果用户希望根据报文目的地址所属ISP网络选择相应的出接口,并根据多出口策略路由进行智能的选路,实现链路资源的合理利用,可以使用该场景。 |
| ISP选路+全局选路策略+DNS透明代理组合场景 | 当内网用户通过域名访问Web服务器时,可以使用该场景。通过配置DNS透明代理,可以使DNS请求报文根据选择的出接口,修改DNS请求报文的目的地址(DNS服务器地址)。通过配置ISP选路和全局选路策略,FW根据报文目的地址所属ISP网络选择相应的出接口,并根据全局选路策略,实现链路资源的合理利用。 |
为了提高流量转发的可靠性,ISP选路功能可以配合健康检查功能一起使用,保证流量不被转发到故障链路上。当健康检查的结果显示链路故障时,对应的ISP路由表项将被删除,所以流量不会命中该条路由,也就避免被转发到故障链路上。当链路状态恢复正常时,对应的ISP路由表项将重新生成,流量即可按此路由进行转发。
Web举例:配置ISP选路实现报文按运营商转发
介绍通过配置ISP选路实现报文按运营商转发的配置举例。
组网需求
如图1所示,FW作为安全网关部署在网络出口,企业分别从ISP1和ISP2租用一条链路。
- 企业希望访问Server 1的报文从ISP1链路转发,访问Server 2的报文从ISP2链路转发。
- 当其中一条链路故障时,后续流量可以通过另一条链路转发,保证传输的可靠性。
配置思路
- 配置健康检查功能,分别为ISP1和ISP2链路配置健康检查。
- 配置接口的IP地址、安全区域和网关地址,并在接口上应用健康检查。
- 制作isp1.csv和isp2.csv两个ISP地址文件,将Server 1的IP地址3.3.3.3写入isp1.csv文件中;将Server 2的IP地址9.9.9.9写入isp2.csv文件中,并上传到FW上。
- 配置ISP选路功能,使访问Server 1的报文从ISP1链路转发,访问Server 2的报文从ISP2链路转发。
- 配置基本的安全策略,允许企业内部用户访问外网资源。

本例着重介绍ISP选路相关的配置,其余配置如NAT请根据实际组网进行配置。
操作步骤
- 为ISP1和ISP2链路分别新建一个健康检查。选择“对象 > 健康检查”,在“健康检查列表”区域单击“新建”,为ISP1链路新建一个健康检查。

 单击“新建”,为ISP2链路新建一个健康检查。
单击“新建”,为ISP2链路新建一个健康检查。
 此处假设3.3.10.10、3.3.10.11和9.9.20.20、9.9.20.21分别为ISP1和ISP2网络中已知的设备地址。如果健康检查配置完后,状态一直为down,请检查健康检查的配置。对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。
此处假设3.3.10.10、3.3.10.11和9.9.20.20、9.9.20.21分别为ISP1和ISP2网络中已知的设备地址。如果健康检查配置完后,状态一直为down,请检查健康检查的配置。对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。 - 制作isp1.csv和isp2.csv两个ISP地址文件,将Server 1的IP地址3.3.3.3写入isp1.csv文件中;将Server 2的IP地址9.9.9.9写入isp2.csv文件中,并上传到FW上。选择“网络 > 路由 > 智能选路”,在“运营商地址库”页签,单击“导入”。
 为ISP1和ISP2分别创建运营商名称isp1_ifgroup和isp2_ifgroup,并导入对应的ISP地址文件。
为ISP1和ISP2分别创建运营商名称isp1_ifgroup和isp2_ifgroup,并导入对应的ISP地址文件。

- 配置接口GigabitEthernet 1/0/1和GigabitEthernet 1/0/7的IP地址和网关地址,加入Untrust安全区域,选择所属运营商,启用运营商路由,并应用对应的健康检查。选择“网络 > 接口”,单击待配置的接口所在行的
 。
。

- 配置接口GigabitEthernet 1/0/3的IP地址,并加入Trust安全区域。选择“网络 > 接口”,单击待配置的接口所在行的
 。
。
- 配置Local到Untrust区域的安全策略,允许FW向目的设备发送相应的健康检查探测报文。
 对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。选择“策略 > 安全策略 > 安全策略”,单击“新建安全策略”。
对于V500R001C80之前的版本,需要在FW上配置对应的安全策略,允许FW向目的设备发送健康检查探测报文。对于V500R001C80及之后的版本,健康检查的探测报文不受安全策略控制,默认放行,无需配置相应安全策略。选择“策略 > 安全策略 > 安全策略”,单击“新建安全策略”。
- 配置Trust到Untrust区域的安全策略,允许企业内网用户访问外网资源。假设内部用户网段为10.3.0.0/24。选择“策略 > 安全策略 > 安全策略”,单击“新建安全策略”。

配置脚本
# isp name isp1_ifgroup set filename isp1.csv isp name isp2_ifgroup set filename isp2.csv # healthcheck enable healthcheck name isp1_health destination 3.3.10.10 interface GigabitEthernet1/0/1 protocol tcp-simple destination-port 10001 destination 3.3.10.11 interface GigabitEthernet1/0/1 protocol tcp-simple destination-port 10002 healthcheck name isp2_health destination 9.9.20.20 interface GigabitEthernet1/0/7 protocol tcp-simple destination-port 10003 destination 9.9.20.21 interface GigabitEthernet1/0/7 protocol tcp-simple destination-port 10004 # interface GigabitEthernet1/0/1 ip address 1.1.1.1 255.255.255.0 healthcheck isp1_health gateway 1.1.1.254 # interface GigabitEthernet1/0/3 ip address 10.3.0.1 255.255.255.0 # interface GigabitEthernet1/0/7 ip address 2.2.2.2 255.255.255.0 healthcheck isp2_health gateway 2.2.2.254 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/3 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/1 add interface GigabitEthernet1/0/7 # security-policy rule name policy_sec_local_untrust source-zone local destination-zone untrust destination-address 3.3.10.10 mask 255.255.255.255 destination-address 3.3.10.11 mask 255.255.255.255 destination-address 9.9.20.20 mask 255.255.255.255 destination-address 9.9.20.21 mask 255.255.255.255 service tcp action permit rule name policy_sec_trust_untrust source-zone trust destination-zone untrust source-address 10.3.0.0 mask 255.255.255.0 action permit # interface-group 1 isp isp1_ifgroup add interface GigabitEthernet1/0/1 # interface-group 2 isp isp2_ifgroup add interface GigabitEthernet1/0/7 # return
*************************本案例配置文件***********************
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW]dis cu |
| !Software Version V200R003C00SPC300 |
| # |
| sysname NW_L3SW |
| # |
| vlan batch 10 100 3999 |
| # |
| diffserv domain default |
| # |
| aaa |
| authentication-scheme default |
| authorization-scheme default |
| accounting-scheme default |
| domain default |
| domain default_admin |
| local-user admin password cipher %@%@5d~9:M^ipCfL\iB)EQd>3Uwe%@%@ |
| local-user admin service-type http |
| # |
| interface Vlanif1 |
| # |
| interface Vlanif10 |
| ip address 172.16.10.1 255.255.255.0 |
| # |
| interface Vlanif100 |
| description link-to-FW |
| ip address 10.1.1.1 255.255.255.252 |
| # |
| interface MEth0/0/1 |
| # |
| interface GigabitEthernet0/0/1 |
| description Link-to-PC |
| port link-type access |
| port default vlan 10 |
| # |
| interface GigabitEthernet0/0/2 |
| port link-type access |
| port default vlan 10 |
| # |
| interface GigabitEthernet0/0/3 |
| port link-type access |
| port default vlan 10 |
| # |
| interface GigabitEthernet0/0/4 |
| port link-type access |
| port default vlan 10 |
| # |
| interface GigabitEthernet0/0/5 |
| port link-type access |
| port default vlan 10 |
| # |
| interface GigabitEthernet0/0/6 |
| port link-type access |
| port default vlan 10 |
| # |
| interface GigabitEthernet0/0/7 |
| # |
| interface GigabitEthernet0/0/8 |
| # |
| interface GigabitEthernet0/0/9 |
| # |
| interface GigabitEthernet0/0/10 |
| # |
| interface GigabitEthernet0/0/11 |
| # |
| interface GigabitEthernet0/0/12 |
| # |
| interface GigabitEthernet0/0/13 |
| # |
| interface GigabitEthernet0/0/14 |
| # |
| interface GigabitEthernet0/0/15 |
| # |
| interface GigabitEthernet0/0/16 |
| # |
| interface GigabitEthernet0/0/17 |
| # |
| interface GigabitEthernet0/0/18 |
| # |
| interface GigabitEthernet0/0/19 |
| # |
| interface GigabitEthernet0/0/20 |
| # |
| interface GigabitEthernet0/0/21 |
| # |
| interface GigabitEthernet0/0/22 |
| # |
| interface GigabitEthernet0/0/23 |
| # |
| interface GigabitEthernet0/0/24 |
| # |
| interface GigabitEthernet0/0/25 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/26 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/27 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/28 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/29 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/30 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/31 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/32 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/33 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/34 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/35 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/36 |
| port link-type access |
| port default vlan 3999 |
| stp edged-port enable |
| # |
| interface GigabitEthernet0/0/37 |
| # |
| interface GigabitEthernet0/0/38 |
| # |
| interface GigabitEthernet0/0/39 |
| # |
| interface GigabitEthernet0/0/40 |
| # |
| interface GigabitEthernet0/0/41 |
| # |
| interface GigabitEthernet0/0/42 |
| # |
| interface GigabitEthernet0/0/43 |
| # |
| interface GigabitEthernet0/0/44 |
| # |
| interface GigabitEthernet0/0/45 |
| # |
| interface GigabitEthernet0/0/46 |
| # |
| interface GigabitEthernet0/0/47 |
| # |
| interface GigabitEthernet0/0/48 |
| port link-type access |
| port default vlan 100 |
| # |
| interface XGigabitEthernet0/0/1 |
| # |
| interface XGigabitEthernet0/0/2 |
| # |
| interface XGigabitEthernet0/0/3 |
| # |
| interface XGigabitEthernet0/0/4 |
| # |
| interface NULL0 |
| # |
| ip route-static 0.0.0.0 0.0.0.0 10.1.1.2 |
| # |
| snmp-agent |
| snmp-agent local-engineid 800007DB03FCE33CACD040 |
| snmp-agent community read cipher %$%$l|);R}U>F&[7Dp,]Y`F%AKZKVYWd+|&$a9xb\v#-.l8VKZNAziP0G#za|UL>J@FhID6#ZWAK%$%$ |
| snmp-agent sys-info version v2c v3 |
| # |
| user-interface con 0 |
| user-interface vty 0 4 |
| user-interface vty 16 20 |
| # |
| return |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| [NW_L3SW] |
| <HuaweiFW> |
| <HuaweiFW> |
| <HuaweiFW>dis cu |
| 2025-09-28 12:04:14.930 +08:00 |
| !Software Version V500R005C20SPC500 |
| # |
| sysname HuaweiFW |
| # |
| l2tp domain suffix-separator @ |
| # |
| authentication-profile name portal_authen_default |
| # |
| undo factory-configuration prohibit |
| # |
| undo telnet server enable |
| undo telnet ipv6 server enable |
| # |
| clock timezone Beijing add 08:00:00 |
| # |
| update schedule location-sdb weekly Sun 06:15 |
| # |
| firewall defend action discard |
| # |
| log type traffic enable |
| log type syslog enable |
| log type policy enable |
| # |
| undo dataflow enable |
| # |
| undo sa force-detection enable |
| # |
| isp name isp1 set filename ISP1.csv |
| isp name isp2 set filename ISP2.csv |
| # |
| banner enable |
| # |
| slb enable |
| # |
| user-manage web-authentication security port 8887 |
| undo privacy-statement english |
| undo privacy-statement chinese |
| page-setting |
| user-manage security version tlsv1.1 tlsv1.2 |
| password-policy |
| level high |
| # |
| firewall ids authentication type aes256 |
| # |
| icmp ttl-exceeded send |
| icmp echo-reply fast enable |
| # |
| web-manager security version tlsv1.1 tlsv1.2 |
| web-manager enable |
| web-manager security enable |
| undo web-manager config-guide enable |
| # |
| firewall dataplane to manageplane application-apperceive default-action drop |
| # |
| undo ips enhanced enable |
| # |
| feedback type threat-log enable |
| feedback type pdns enable |
| # |
| update schedule ips-sdb daily 23:21 |
| update schedule av-sdb daily 23:21 |
| update schedule sa-sdb daily 23:21 |
| update schedule ip-reputation daily 23:21 |
| update schedule cnc daily 23:21 |
| update schedule file-reputation daily 23:21 |
| update schedule ext-url-sdb daily 06:58 |
| # |
| set disk-scan parameter attach on |
| set disk-scan parameter cycle 15 |
| set disk-scan parameter iostat 80 |
| set disk-scan parameter speed 10 |
| set disk-scan parameter switch on |
| set disk-scan parameter parallel 50 |
| disk-usage alarm threshold 95 |
| # |
| ip vpn-instance default |
| ipv4-family |
| # |
| healthcheck enable |
| healthcheck name ISP1 |
| source-ip 1.32.3.1 |
| destination 1.32.3.10 interface GigabitEthernet1/0/1 next-hop 1.32.3.10 protocol icmp |
| healthcheck name ISP2 |
| source-ip 2.32.3.1 |
| destination 2.32.3.10 interface GigabitEthernet1/0/2 next-hop 2.32.3.10 protocol icmp |
| # |
| ip address-set 互联网接口IP type object |
| address 0 117.32.3.1 mask 32 |
| # |
| ip address-set CQ分支机构IP type object |
| address 0 range 192.168.10.1 192.168.10.254 |
| address 1 range 172.16.100.2 172.16.100.100 |
| # |
| ip address-set 总部业务IP type object |
| address 0 range 172.16.10.1 172.16.10.254 |
| # |
| ip address-set SSLVPN网络扩展资源客户端IP type object |
| address 0 range 172.16.200.1 172.16.200.200 |
| # |
| ip address-set 感兴趣流 type object |
| address 0 172.16.10.0 mask 24 |
| # |
| ip address-set 感兴趣流源IP_业务1 type object |
| address 0 172.16.10.0 mask 24 |
| # |
| ip address-set 感兴趣流目的IP_业务1 type object |
| address 0 192.168.10.0 mask 24 |
| # |
| ip address-set 建立VPN隧道的源地址 type object |
| address 0 117.32.3.1 mask 32 |
| # |
| ip address-set 建立VPN隧道的目的地址 type object |
| address 0 117.32.3.10 mask 32 |
| # |
| ip address-set FTP真实服务器地址 type object |
| address 0 range 172.16.10.1 172.16.10.200 |
| # |
| ip address-set FTP服务VIP地址 type object |
| address 0 117.32.3.2 mask 32 |
| address 1 117.32.3.1 mask 32 |
| # |
| ip address-set FTP服务器VIP type object |
| address 0 117.32.3.2 mask 32 |
| # |
| time-range worktime |
| period-range 08:00:00 to 18:00:00 working-day |
| # |
| acl number 3000 |
| rule 5 permit ip source address-set 感兴趣流源IP_业务1 destination address-set 感兴趣流目的IP_业务1 |
| # |
| ipsec proposal prop21995140294 |
| esp authentication-algorithm sha1 |
| esp encryption-algorithm 3des |
| # |
| ike proposal default |
| encryption-algorithm aes-256 aes-192 aes-128 |
| dh group14 |
| authentication-algorithm sha2-512 sha2-384 sha2-256 |
| authentication-method pre-share |
| integrity-algorithm hmac-sha2-256 |
| prf hmac-sha2-256 |
| ike proposal 1 |
| encryption-algorithm 3des |
| dh group2 |
| authentication-algorithm sha1 |
| authentication-method pre-share |
| integrity-algorithm hmac-sha2-256 |
| prf hmac-sha2-256 |
| # |
| ike peer ike21995140294 |
| undo version 2 |
| exchange-mode auto |
| pre-shared-key %^%#`n};A)f~p;!$wi!q5iEIy8;fPj-dq.>eA0$_lvrI%^%# |
| ike-proposal 1 |
| remote-id-type none |
| local-id 117.32.3.1 |
| dpd type periodic |
| remote-address 117.32.3.10 |
| rsa encryption-padding oaep |
| rsa signature-padding pss |
| local-id-preference certificate enable |
| ikev2 authentication sign-hash sha2-256 |
| # |
| ipsec policy ipsec2199514012 1 isakmp |
| security acl 3000 |
| ike-peer ike21995140294 |
| proposal prop21995140294 |
| tunnel local applied-interface |
| undo policy enable |
| alias IPSEC_to_H3CRouter |
| sa trigger-mode auto |
| sa duration traffic-based 5242880 |
| sa duration time-based 3600 |
| # |
| web-auth-server default |
| port 50100 |
| # |
| portal-access-profile name default |
| # |
| ip pool pool |
| section 0 172.16.100.2 172.16.100.100 |
| # |
| aaa |
| authentication-scheme admin_ad |
| authentication-scheme admin_ad_local |
| authentication-scheme admin_hwtacacs |
| authentication-scheme admin_hwtacacs_local |
| authentication-scheme admin_ldap |
| authentication-scheme admin_ldap_local |
| authentication-scheme admin_local |
| authentication-scheme admin_radius |
| authentication-scheme admin_radius_local |
| authentication-scheme default |
| authorization-scheme default |
| accounting-scheme default |
| domain default |
| service-type internetaccess ssl-vpn l2tp ike |
| internet-access mode password |
| reference user current-domain |
| manager-user audit-admin |
| password cipher $1a$Vg0H:|1TH)$c/eA0.a335K6l1+u)c7*L+`m%}a\~.\Ep)Tt2q0($ |
| service-type web terminal |
| level 15 |
| <ISP1> |
| <ISP1> |
| <ISP1>dis cu |
| # |
| version 7.1.064, Release 0707P16 |
| # |
| sysname ISP1 |
| # |
| ospf 1 router-id 1.1.1.5 |
| import-route direct |
| area 0.0.0.0 |
| network 1.1.1.2 0.0.0.0 |
| network 1.1.1.5 0.0.0.0 |
| # |
| ip unreachables enable |
| ip ttl-expires enable |
| # |
| password-recovery enable |
| # |
| vlan 1 |
| # |
| controller Cellular0/0 |
| # |
| interface Virtual-PPP1 |
| ppp chap password cipher $c$3$7+JsxvAZR/bo5k3VQVojUdH041O4G8TW+rtP2gCv |
| ppp chap user user0002 |
| ppp pap local-user user0001 password cipher $c$3$qmbMgjjDA/VzdLSGyc6l+WmjS8aFg+e97Nihjxhf |
| ip address ppp-negotiate |
| l2tp-auto-client l2tp-group 1 |
| nat outbound |
| # |
| interface NULL0 |
| # |
| interface Ethernet0/3 |
| port link-mode bridge |
| # |
| interface Ethernet0/4 |
| port link-mode bridge |
| # |
| interface Ethernet0/5 |
| port link-mode bridge |
| # |
| interface Ethernet0/6 |
| port link-mode bridge |
| # |
| interface Ethernet0/7 |
| port link-mode bridge |
| # |
| interface Ethernet0/8 |
| port link-mode bridge |
| # |
| interface Ethernet0/9 |
| port link-mode bridge |
| # |
| interface Ethernet0/10 |
| port link-mode bridge |
| # |
| interface Ethernet0/11 |
| port link-mode bridge |
| # |
| interface Ethernet0/12 |
| port link-mode bridge |
| # |
| interface Ethernet0/13 |
| port link-mode bridge |
| # |
| interface Ethernet0/14 |
| port link-mode bridge |
| # |
| interface Ethernet0/15 |
| port link-mode bridge |
| # |
| interface Ethernet0/16 |
| port link-mode bridge |
| # |
| interface Ethernet0/17 |
| port link-mode bridge |
| # |
| interface Ethernet0/18 |
| port link-mode bridge |
| # |
| interface Ethernet0/19 |
| port link-mode bridge |
| # |
| interface Ethernet0/20 |
| port link-mode bridge |
| # |
| interface Ethernet0/21 |
| port link-mode bridge |
| # |
| interface Ethernet0/22 |
| port link-mode bridge |
| # |
| interface Ethernet0/23 |
| port link-mode bridge |
| # |
| interface Ethernet0/24 |
| port link-mode bridge |
| # |
| interface Ethernet0/25 |
| port link-mode bridge |
| # |
| interface Ethernet0/26 |
| port link-mode bridge |
| # |
| interface GigabitEthernet0/0 |
| port link-mode route |
| ip address 1.1.1.5 255.255.255.252 |
| # |
| interface GigabitEthernet0/1 |
| port link-mode route |
| description LinktoFW |
| ip address 1.32.3.10 255.255.255.0 |
| # |
| interface GigabitEthernet0/2 |
| port link-mode route |
| description Link-to-ISP2 |
| ip address 1.1.1.2 255.255.255.252 |
| # |
| interface GigabitEthernet0/27 |
| port link-mode route |
| # |
| scheduler logfile size 16 |
| # |
| line class console |
| user-role network-admin |
| # |
| line class tty |
| user-role network-operator |
| # |
| line class vty |
| user-role network-operator |
| # |
| line con 0 |
| user-role network-admin |
| # |
| line vty 0 63 |
| user-role network-operator |
| # |
| ip route-static 0.0.0.0 0 1.32.3.1 |
| ip route-static 22.22.22.22 32 1.1.1.6 |
| # |
| domain system |
| # |
| domain default enable system |
| # |
| role name level-0 |
| description Predefined level-0 role |
| # |
| role name level-1 |
| description Predefined level-1 role |
| # |
| role name level-2 |
| description Predefined level-2 role |
| # |
| role name level-3 |
| description Predefined level-3 role |
| # |
| role name level-4 |
| description Predefined level-4 role |
| # |
| role name level-5 |
| description Predefined level-5 role |
| # |
| role name level-6 |
| description Predefined level-6 role |
| # |
| role name level-7 |
| description Predefined level-7 role |
| # |
| role name level-8 |
| description Predefined level-8 role |
| # |
| role name level-9 |
| description Predefined level-9 role |
| # |
| role name level-10 |
| description Predefined level-10 role |
| # |
| role name level-11 |
| description Predefined level-11 role |
| # |
| role name level-12 |
| description Predefined level-12 role |
| # |
| role name level-13 |
| description Predefined level-13 role |
| # |
| role name level-14 |
| description Predefined level-14 role |
| # |
| user-group system |
| # |
| l2tp-group 1 mode lac |
| lns-ip 117.32.3.1 |
| tunnel name cqfenzhi |
| tunnel password cipher $c$3$lxEdd6VH206m6NI2dYg+iDARzTWY7IgU/xCC |
| # |
| return |
| <ISP1> |
| <ISP1> |
| <ISP1> |
| <ISP1> |
| <ISP1> |
| <ISP1> |
| <ISP1> |
| <ISP2> |
| #Apr 26 16:15:35:465 2000 ISP2 SHELL/4/LOGIN: |
| Trap 1.3.6.1.4.1.25506.2.2.1.1.3.0.1<hh3cLogIn>: login from Console |
| %Apr 26 16:15:35:606 2000 ISP2 SHELL/5/SHELL_LOGIN: Console logged in from aux0. |
| <ISP2> |
| <ISP2> |
| <ISP2> |
| <ISP2>dis cu |
| # |
| version 5.20, Release 1206 |
| # |
| sysname ISP2 |
| # |
| irf mac-address persistent timer |
| irf auto-update enable |
| undo irf link-delay |
| # |
| domain default enable system |
| # |
| telnet server enable |
| # |
| ip ttl-expires enable |
| ip unreachables enable |
| # |
| vlan 1 |
| # |
| radius scheme system |
| server-type extended |
| primary authentication 127.0.0.1 1645 |
| primary accounting 127.0.0.1 1646 |
| user-name-format without-domain |
| # |
| domain system |
| access-limit disable |
| state active |
| idle-cut disable |
| self-service-url disable |
| # |
| user-group system |
| # |
| interface NULL0 |
| # |
| interface GigabitEthernet1/0/1 |
| port link-mode route |
| ip address 2.32.3.10 255.255.255.0 |
| # |
| interface GigabitEthernet1/0/10 |
| port link-mode route |
| ip address 1.1.1.6 255.255.255.252 |
| # |
| interface GigabitEthernet1/0/48 |
| port link-mode route |
| ip address 2.2.2.2 255.255.255.252 |
| # |
| interface GigabitEthernet1/0/2 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/3 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/4 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/5 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/6 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/7 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/8 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/9 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/11 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/12 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/13 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/14 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/15 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/16 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/17 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/18 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/19 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/20 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/21 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/22 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/23 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/24 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/25 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/26 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/27 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/28 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/29 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/30 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/31 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/32 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/33 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/34 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/35 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/36 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/37 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/38 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/39 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/40 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/41 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/42 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/43 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/44 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/45 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/46 |
| port link-mode bridge |
| # |
| interface GigabitEthernet1/0/47 |
| port link-mode bridge |
| # |
| interface Ten-GigabitEthernet1/0/49 |
| port link-mode bridge |
| # |
| interface Ten-GigabitEthernet1/0/50 |
| port link-mode bridge |
| # |
| interface Ten-GigabitEthernet1/0/51 |
| port link-mode bridge |
| # |
| interface Ten-GigabitEthernet1/0/52 |
| port link-mode bridge |
| # |
| ospf 1 router-id 1.1.1.6 |
| import-route direct |
| area 0.0.0.0 |
| network 1.1.1.6 0.0.0.0 |
| network 2.2.2.2 0.0.0.0 |
| # |
| ip route-static 0.0.0.0 0.0.0.0 2.32.3.1 |
| ip route-static 11.11.11.11 255.255.255.255 1.1.1.5 |
| # |
| load xml-configuration |
| # |
| user-interface aux 0 |
| user-interface vty 0 15 |
| user privilege level 3 |
| set authentication password simple 123456 |
| idle-timeout 0 0 |
| # |
| return |
| <ISP2> |
| <ISP2> |
| <ISP2> |
| <ISP2> |
| <ISP2> |
| <ISP2> |
| <ISP2> |
| <ISP2> |
| <TargetServer>dis cu |
| !Software Version V200R003C00SPC300 |
| # |
| sysname TargetServer |
| # |
| vlan batch 10 20 111 |
| # |
| aaa |
| authentication-scheme default |
| authorization-scheme default |
| accounting-scheme default |
| domain default |
| domain default_admin |
| local-user admin password cipher %@%@5d~9:M^ipCfL\iB)EQd>3Uwe%@%@ |
| local-user admin service-type http |
| # |
| interface Vlanif1 |
| # |
| interface Vlanif10 |
| ip address 1.1.1.1 255.255.255.252 |
| # |
| interface Vlanif20 |
| ip address 2.2.2.1 255.255.255.252 |
| # |
| interface MEth0/0/1 |
| # |
| interface GigabitEthernet0/0/1 |
| # |
| interface GigabitEthernet0/0/2 |
| port link-type access |
| port default vlan 10 |
| # |
| interface GigabitEthernet0/0/3 |
| # |
| interface GigabitEthernet0/0/4 |
| # |
| interface GigabitEthernet0/0/5 |
| # |
| interface GigabitEthernet0/0/6 |
| # |
| interface GigabitEthernet0/0/7 |
| # |
| interface GigabitEthernet0/0/8 |
| # |
| interface GigabitEthernet0/0/9 |
| # |
| interface GigabitEthernet0/0/10 |
| # |
| interface GigabitEthernet0/0/11 |
| # |
| interface GigabitEthernet0/0/12 |
| # |
| interface GigabitEthernet0/0/13 |
| # |
| interface GigabitEthernet0/0/14 |
| # |
| interface GigabitEthernet0/0/15 |
| # |
| interface GigabitEthernet0/0/16 |
| # |
| interface GigabitEthernet0/0/17 |
| # |
| interface GigabitEthernet0/0/18 |
| # |
| interface GigabitEthernet0/0/19 |
| # |
| interface GigabitEthernet0/0/20 |
| # |
| interface GigabitEthernet0/0/21 |
| # |
| interface GigabitEthernet0/0/22 |
| # |
| interface GigabitEthernet0/0/23 |
| # |
| interface GigabitEthernet0/0/24 |
| # |
| interface GigabitEthernet0/0/25 |
| # |
| interface GigabitEthernet0/0/26 |
| # |
| interface GigabitEthernet0/0/27 |
| # |
| interface GigabitEthernet0/0/28 |
| # |
| interface GigabitEthernet0/0/29 |
| # |
| interface GigabitEthernet0/0/30 |
| # |
| interface GigabitEthernet0/0/31 |
| # |
| interface GigabitEthernet0/0/32 |
| # |
| interface GigabitEthernet0/0/33 |
| # |
| interface GigabitEthernet0/0/34 |
| # |
| interface GigabitEthernet0/0/35 |
| # |
| interface GigabitEthernet0/0/36 |
| # |
| interface GigabitEthernet0/0/37 |
| # |
| interface GigabitEthernet0/0/38 |
| # |
| interface GigabitEthernet0/0/39 |
| # |
| interface GigabitEthernet0/0/40 |
| # |
| interface GigabitEthernet0/0/41 |
| # |
| interface GigabitEthernet0/0/42 |
| # |
| interface GigabitEthernet0/0/43 |
| # |
| interface GigabitEthernet0/0/44 |
| # |
| interface GigabitEthernet0/0/45 |
| # |
| interface GigabitEthernet0/0/46 |
| # |
| interface GigabitEthernet0/0/47 |
| # |
| interface GigabitEthernet0/0/48 |
| port link-type access |
| port default vlan 20 |
| # |
| interface XGigabitEthernet0/1/1 |
| # |
| interface XGigabitEthernet0/1/2 |
| # |
| interface NULL0 |
| # |
| interface LoopBack0 |
| ip address 11.11.11.11 255.255.255.255 |
| # |
| interface LoopBack1 |
| ip address 22.22.22.22 255.255.255.255 |
| # |
| ospf 1 router-id 11.11.11.11 |
| import-route direct |
| area 0.0.0.0 |
| network 1.1.1.1 0.0.0.0 |
| network 2.2.2.1 0.0.0.0 |
| # |
| ip route-static 1.32.3.0 255.255.255.0 1.1.1.2 |
| ip route-static 2.32.3.0 255.255.255.0 2.2.2.2 |
| # |
| user-interface con 0 |
| user-interface vty 0 4 |
| user-interface vty 16 20 |
| # |
| return |
| <TargetServer> |
| <TargetServer> |
| <TargetServer> |
| <TargetServer> |
| <TargetServer> |


